New Industrial Spy stolen data market promoted through cracks, adware

Menace actors have launched a new market referred to as Industrial Spy that sells stolen info from breached businesses, as effectively as featuring cost-free stolen data to its members.
While stolen information marketplaces are not new, instead of extorting organizations and scaring them with GDPR fines, Industrial Spy promotes itself as a market wherever enterprises can obtain their competitors’ info to achieve access to trade tricks, producing diagrams, accounting experiences, and client databases.
Nonetheless, it would not be stunning if the marketplace is made use of to extort victims into getting their info to avert it from being bought to other menace actors.
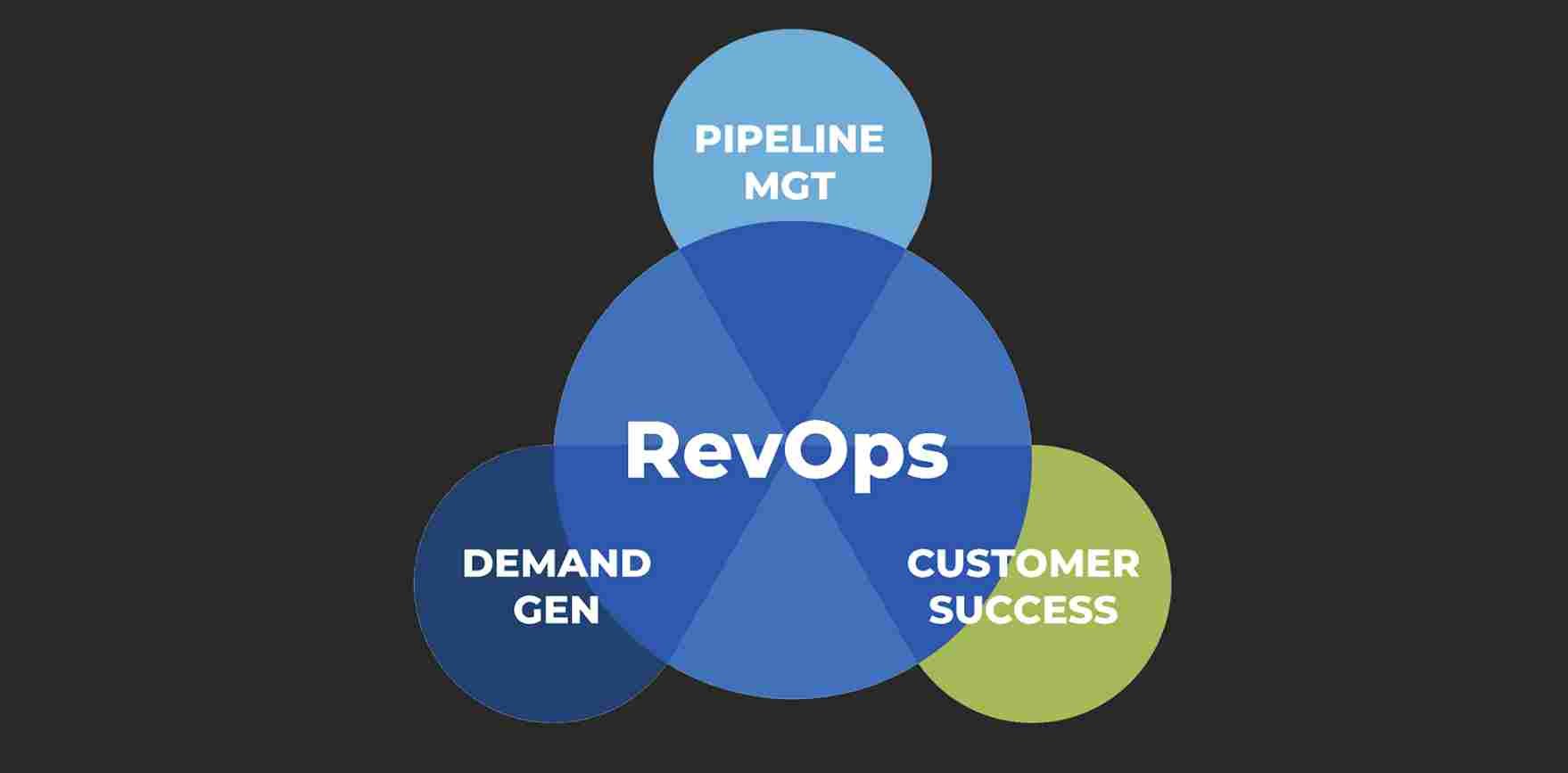
The Industrial Spy marketplace features distinct tiers of facts choices, with “quality” stolen details offers costing millions of dollars and reduce-tier knowledge that can be bought as individual data files for as very little as $2.
For illustration, Industrial Spy is at the moment providing an Indian firm’s knowledge in their top quality class for $1.4 million, paid in bitcoin.
Resource: BleepingComputer
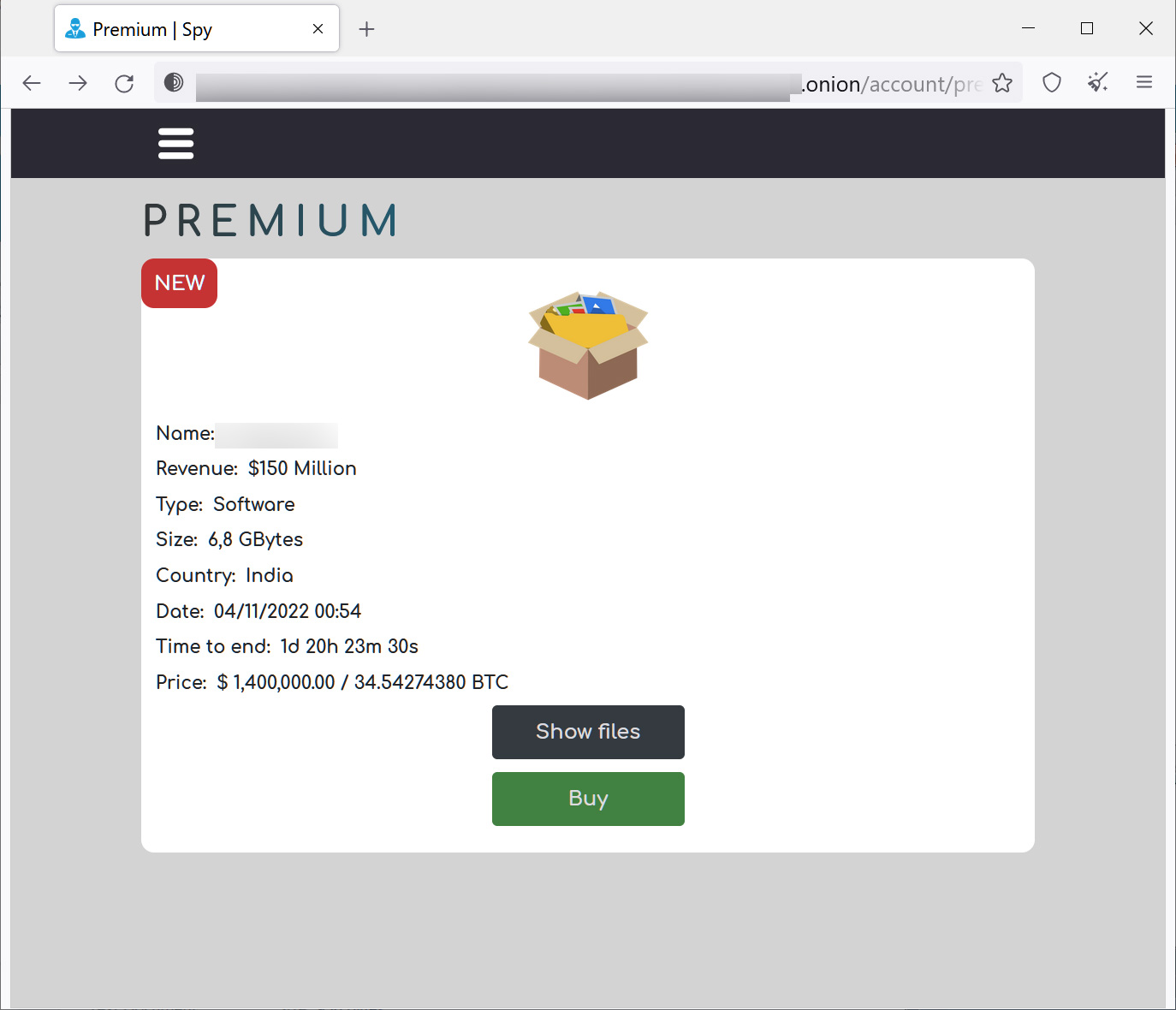
However, a great deal of their knowledge is staying sold as personal data files, wherever danger actors can order the unique data files they want for $2 each individual.
Source: BleepingComputer
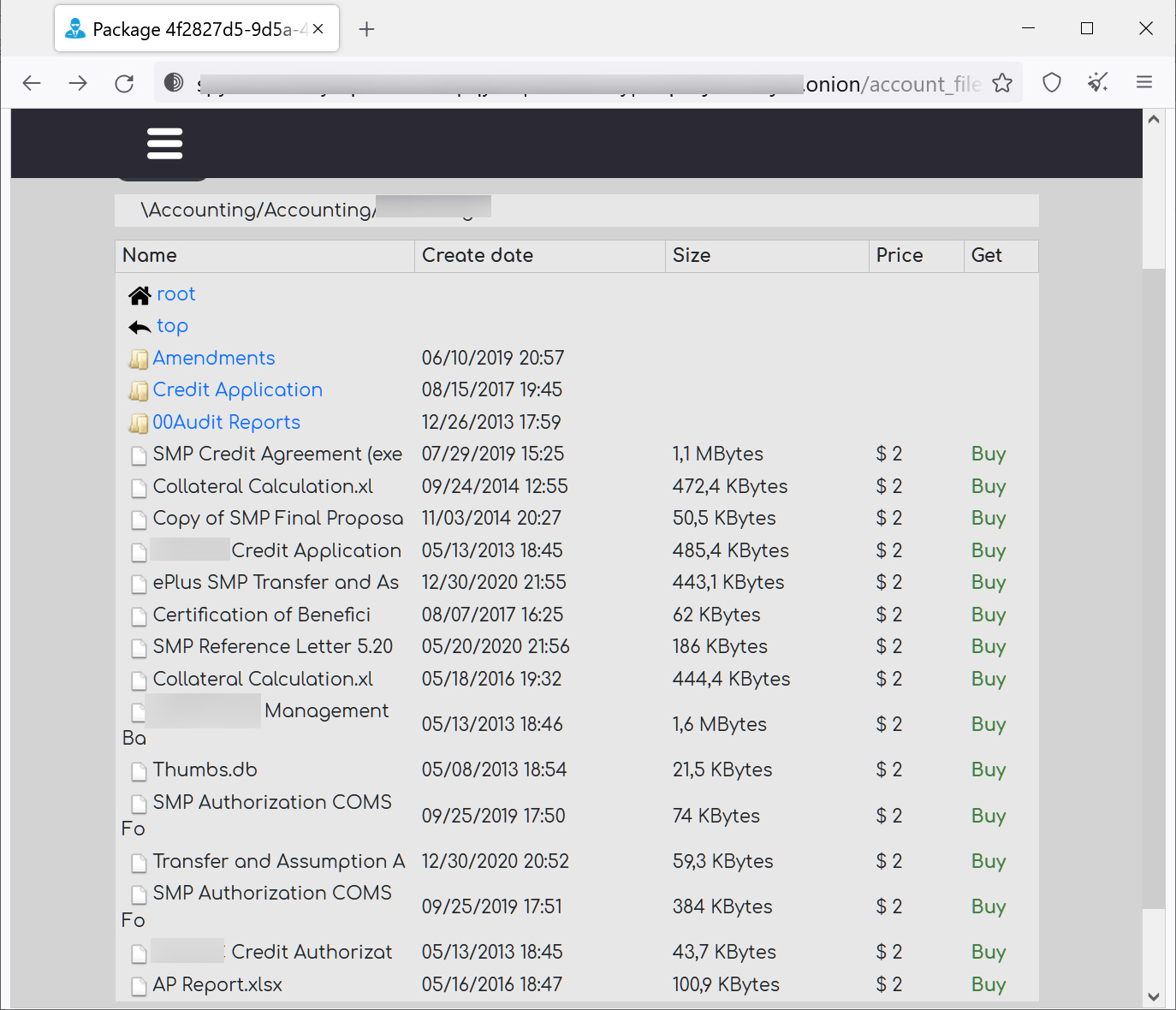
The marketplace also provides absolutely free stolen information packs, probable to entice other menace actors to use the site.
Some of the organizations whose data is presented in the “Basic” classification are regarded to have experienced ransomware assaults in the previous.
Consequently, the threat actors may perhaps have downloaded this information from ransomware gang’s leak web sites to resell on Industrial Spy.
Promoted by way of cracks and adware
BleepingComputer first uncovered of the Industrial Spy marketplace from protection researcher MalwareHunterTeam, who identified malware executables [1, 2] that make README.txt data files to advertise the website.
When executed, these malware information will generate the textual content information in each individual folder on the gadget, containing a description of the assistance and a url to the Tor site.
“There you can buy or down load for cost-free private and compromising facts of your opponents. We general public strategies, drawings, technologies, political and armed forces insider secrets, accounting studies and clientele databases,” reads the README.txt textual content file.
“All this issues have been collected from the biggest around the globe companies, conglomerates and concerns with each and every action. We collect information making use of vunlerability in their IT infrastructure.”
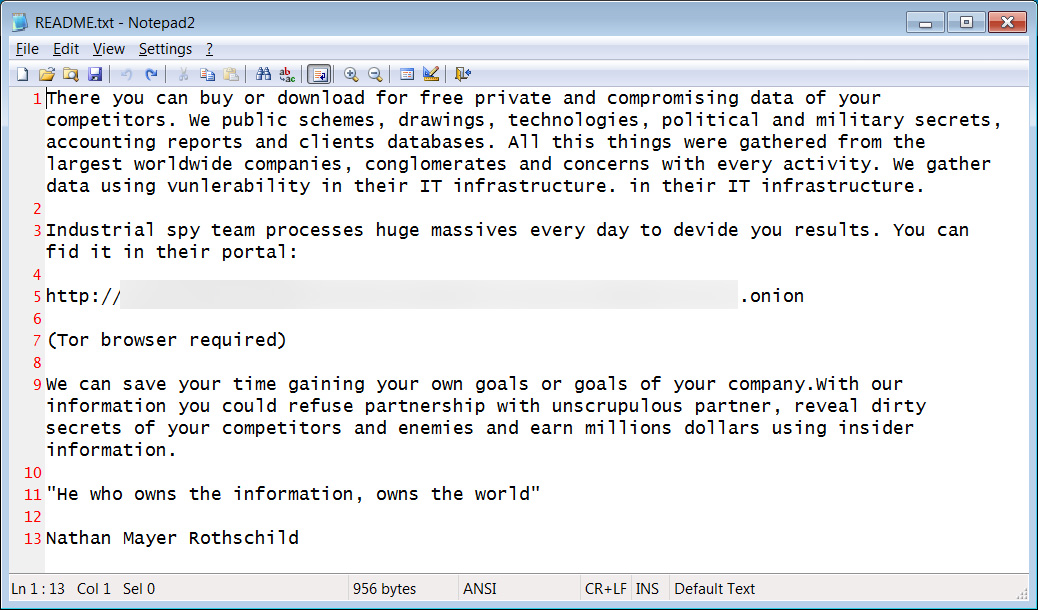
Resource: BleepingComputer
On further more investigation by BleepingComputer, we uncovered that these executables are getting distributed through other malware downloaders usually disguised as cracks and adware.
For instance, the Stop ransomware and password-stealing Trojans, normally dispersed through cracks, are mounted along with the Industrial Spy executables.
On top of that, VirusTotal demonstrates that the README.txt information are discovered in several collections of password-stealing trojan logs, indicating that each courses were being operate on the identical machine.
This suggests that the operators of the Industrial Spy web page probably lover with adware and crack distributors to distribute the program that promotes the marketplace.
While the web-site is not greatly utilised at this level, corporations and safety researchers have to have to continue to keep an eye on it and the knowledge it purports to offer.